The bottom line: I didn’t get your E-Mail last week, please re-send it. Sorry about that.
Here’s the story:
I’m in the process of consolidating my DNS names/services at http://Hover.com. Hover.com is retail side of the Canadian internet stalwart TuCows.com.
Hover offers a service for $25 for their concierge to handle DNS address transfers to Hover. I opted in, as I had previously transferred some domains and the “locking” etc. was a little tricky and with the address http://passnerd.com , http://rimcount.com , http://timelesstweet.com , http://clurko.com and http://lindsayclare.ca were all at A2Webhosting.com and http://mattclare.ca was at http://CanReg.com. I always knew .ca would be a problem, but I had no idea how big it would be..
I had called Hover’s toll-free number two weeks before mattclare.ca expired. It sounded like lots of time as we talked through the plan.
I sent my concierge at Hover my passwords and he changed the contact E-Mail at A2WebHosting to his own. The .com address were transferred to Hover very quickly without issue.
CanReg refused to send the transfer E-Mails to my concierge’s E-Mail address, despite appearances from their web interface to suggest everything had been changed. CanReg kept sending E-Mails to my @mattclare.ca address. We both tried, but despite a number of changes in a number of locations the transfer details were always being sent to @mattclare.ca
The transfer was started on a Friday in the early afternoon. My concierge warned me by E-Mail that he was about to start and shortly after the transfer E-Mail showed up. I wasn’t able to check my E-Mail that afternoon until 5:30 that night and even though Hover is open 8:00 to 8:00, they apparently don’t hand-off cases. My E-Mail sat in my concierge’s inbox through the Sunday expiration of my mattclare.ca domain.
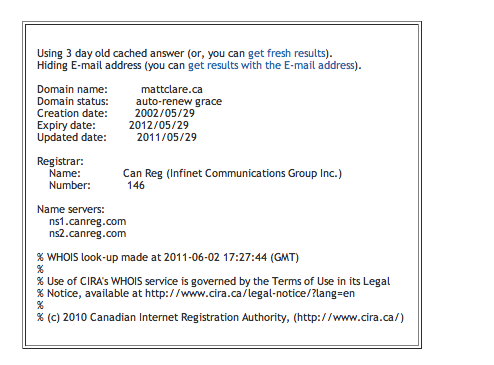 CanReg put my site in “auto-renew grace” which basically told the rest of the internet that they know about mattclare.ca, but didn’t know where to direct anyone. CanReg also kept sending all of their transfer e-mails to my @mattclare.ca address, which they had taken off-line. Thanks.
CanReg put my site in “auto-renew grace” which basically told the rest of the internet that they know about mattclare.ca, but didn’t know where to direct anyone. CanReg also kept sending all of their transfer e-mails to my @mattclare.ca address, which they had taken off-line. Thanks.
By Tuesday my concierge (with my help) fully understood the challenge that now faced us. With my encouragement, my concierge got in touch of with CanReg on Tuesday. CanReg indicated that if I wanted my E-Mail changed it would require a signed and witnessed document, plus government ID, to be faxed or scanned plus E-Mailed to them.
Today I sent an “or-else” E-Mail to my concierge who suggested that if I did renew with CanReg Hover wouldn’t charge me for that domain (I assume for a year). I did renew with CanReg (at a twice the price of Hover) and that’s how I got my mattclare.ca domain back. Perhaps I should have done this last week, but I really didn’t think this would be so hard to complete.
So now CanReg’s insistence on sending transfer E-Mails to my @mattclare.ca will at least be received.
I’m pretty frustrated, but I’m not exactly sure where to direct that frustration. Here’s hoping being a Hover customer gets better from here.
Update: Tuesday June 7, 2011 10:06 AM
Hover has completed the transfer and is neither charging me for the mattclare.ca registration or their concierge fee. Seems like the best thing they could do at this point. I suppose it’s not a happy ending unless there’s some drama along the way.