A recent article in the Columbia Journalism Review by Matthieu Aikins underscored the need to protect the contents of your smartphone. If the potential to have your own information stollen or generally snooped through your stuff, please consider this story.
The British journalist and filmmaker Sean McAllister was in Syriashooting a documentary for Britain’s Channel 4 about the underground there. A few he had worked with were concerned about his general lack of care about his communications and protection of the identities of those in the underground he was working with.
In October, McAllister was detained by Syrian security agents. Well detained he could hear the cries of prisoners being tortured in nearby rooms. He was interrogated and had all of his electronics seized and searched.
Upon hearing that security forces had McCallister a few individuals who had been in touch with, including the main source of the article, immediately fled fearing the brutal Syrian regime now had information that put their lives at risk. Others in McAllister’s electronic records, like one Omar al-Baroudi, were never heard from again.
The article uses the example to point to the need for journalist and the organizations that employ them to become more aware of how to protect their digital information. I hope this stark example will encourage everyone with a smartphone to consider protecting the information on it and information available to it.
If not, please consider the potential embracement of a malevolent or mischievous individual finding your smartphone and posting to Facebook or Twitter on your behalf (though I would understand that it would be nice if someone update your Google Plus account).
It’s not just your data

Your smartphone does not simply have some of your most private information, such as recent phone calls, social networks and E-Mail archives, it has my information too. If your information isn’t enough to convince you to protect the data on your smartphone then please consider the contact information from others that your smartphone contains.
Also consider the information your smartphone could have access to. Following a link in an E-Mail is the only proof of ownership of an account that most sites require when recovering a password. More sophisticated sites with higher security often require more, but would a quick E-Mail to the contact labelled “Mom” in your smartphone about how to spell the name of the street your grew up on yield results?
What you can do to protect the contents of your phone
The best news in all of this is protecting the contents of your smartphone is not that hard.
The type of storage based encryption that can prevent a thief from popping the drive out of your phone and reading it like it was a camera card on another machine is standard on Blackberries, recent iOS devices and is an option on almost all Android-based phones. I don’t know much about Windows Phone 7 Series Phones, but I suspect they are protected by the box they were shipped in.
That said, the most sophisticated encryption won’t protect the contents of your smartphone if all a nefarious individual needs to do is power your smartphone on.
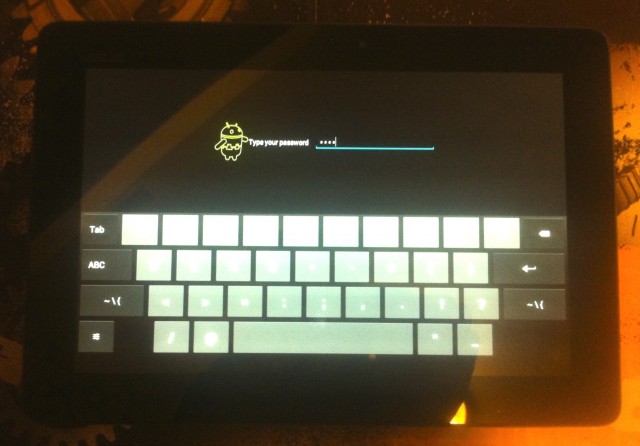
PUT A LOCK CODE ON YOUR SMARTPHONE
Adding a lock code is a huge leap in security over nothing! Even a simple code or Android pattern. If you add a simple code and back that up with the auto erase feature found in the same area of most smartphones you have “good enough” protection. “Good enough” protecting will keep someone who found your phone from pretending to post as you. All iOS and recent Android-based devices backup almost everything on your smartphone to a combination of your computer or “the cloud” and can safely be wiped at any point.
The Electronic Frontier Foundation (EFF) is always a great source for such matters, and they have Surveillance Self-Defense Guide https://ssd.eff.org/your-computer/protect
https://safermobile.org/ is a web site that generally helps people use mobile technology more securely. They have tutorials about how to encrypt the data on your phone and store passwords securely. It’s worth investigating. They even have a guide for journalists.